Physical Inspection of Electronics
The globalization of the semiconductor industry and outsourcing of Integrated Circuit (IC) fabrication to offshore foundries have resulted in critical challenges for the electronics supply chain such as (i) prevalence of counterfeit electronics, (ii) ease of cloning and reverse engineering, (iii) insertion of hardware Trojans, and (iv) development of advanced physical attacks . The physical inspection techniques examine the IC package exterior and interior, and range from simple visual inspection to high-tech imaging solutions that require X-ray microscopy, Infrared imaging, transmission electron microscopy (TEMs), focused ion beams (FIBs), THz imaging, Electron Dispersive Spectroscopy (EDS), etc. The physical inspection requires a thorough analysis of the IC and usually demands using multiple instruments.
a. Multi-modal Inspection with Large-Scale Model
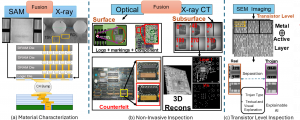
With the advanced imaging capability at SCAN, we have reinforced the capability of large-scale models for physical inspection in multi-modal space. We have distributed the research effort into 3 main arena in this regard – 1. Material Characterization in Advanced Packaging: Single modality data like SAM is not able to detect subtle components like RDL/TSV. We have leveraged features from X-ray using large-scale transformer models to detect those. 2. Non-invasive Inspection: We are further exploring the seamless volumetric reconstruction of PCB by leveraging data from multiple modality. Specifically, PCB X-ray contains noises from heavy metal (e.g. Cu, Pb in Pins/Capacitor) scatteration that inhibits 3D reverse engineering. We are trying to leverage surface level features (SAM/Optical Image) to guide X-ray reconstruction of PCB to reduce scattering effects. 3. Transistor Level Inspection: We further utilize self-supervised learning technique to identify modification at dopant regions with proper explainability.
On top of these, we are currently progressing towards building a large-scale vision-language model, that will direct the learning of trojan features from different modality data with proper node-specific instructions on the trojan type. This will enable diverse trojan/defect feature learning within different node technology and PCB, leading to a physical-inspection oriented AI tool.
b. Reverse Engineering
Reverse engineering (RE) is a process where the goal is to reproduce, duplicate, or enhance chips and systems based on the study of an original object/system. For electronic systems, reverse engineering (RE) could be performed at chip, board, and system levels. Electronic RE intentions include verification of a design for the purposes of quality control, fault and failure analysis, analysis of the features of a competitor’s product, counterfeit detection, Trojan detection, security and trust evaluation, confirmation of intellectual property, approved redesign of an obsolete product, and education.
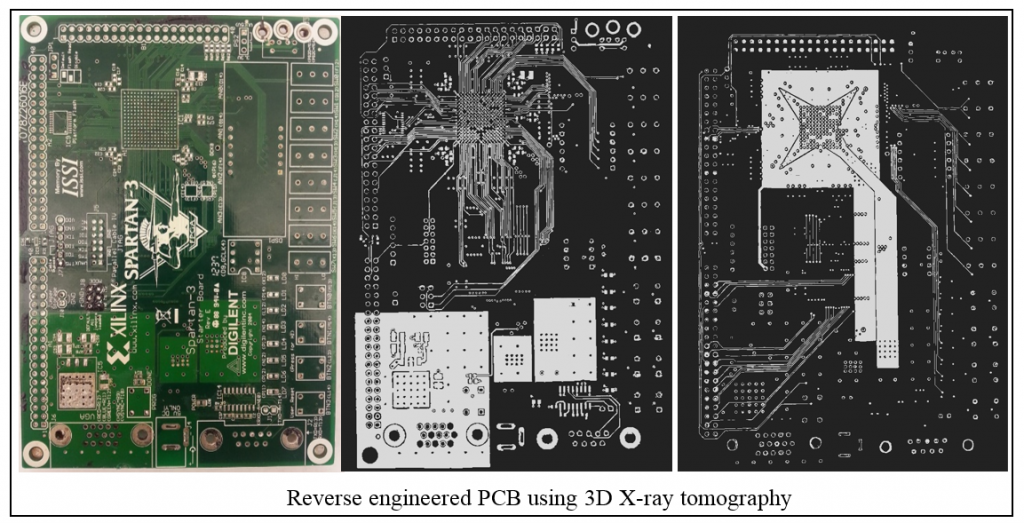
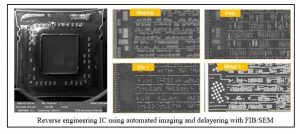
Since such electronics typically consist of multiple layers, reverse engineering involves obtaining the internal structure and connections of all layers through either a destructive process of delayering or non-destructive processes. We have been using X-ray computed tomography to reverse engineer PCBs non-destructively. However, for IC reverse engineering FIB/SEMs are used for delayering large areas (800um by 800um) and collect images automatically.
c. Trojan Scanner
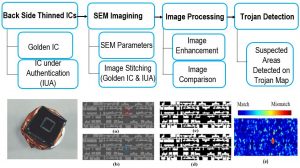
Hardware Trojans are malicious changes to the design of integrated circuits (ICs) at different stages of the design and fabrication processes. Different approaches have been developed to detect Trojans namely non-destructive (electrical tests like run-time monitoring, functional and structural tests) and destructive (full chip reverse engineering). However, these methods cannot detect all types of Trojans and they suffer from a number of disadvantages such as slow speed of detection and lack of confidence in detecting all types of Trojans. Majority of hardware Trojans implemented in an IC will leave a footprint at the doping (active) layer. We have introduced a new concept of “Trojan Scanner” framework for the untrusted foundry threat model, where a trusted GDSII layout (golden layout) is available. Advanced computer vision algorithms in combined with the supervised machine-learning models are used to classify different features of the golden layout and SEM images from an IC under authentication, as a unique descriptor for each type of gates. These descriptors are compared with each other to detect any subtle changes on the active region, which can raise the flag for the existence of a potential hardware Trojan. The descriptors can differentiate variation due to fabrication process, defects, and common SEM image distortions to rule out the possibility of false detection. Our results demonstrate that Trojan Scanner is more reliable than electrical testing and faster than full chip reverse engineering. Trojan Scanner does not rely on the functionality of the circuit rather focuses on the real physical structure to detect malicious changes inserted by the untrusted foundry.
d. Security Assessment
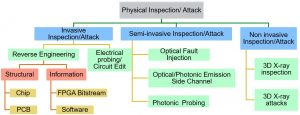
We perform a comprehensive study of the state of knowledge in the field of physical inspection/attacks research and the existing countermeasures. A number of challenges exists for developing trust verification techniques based on invasive, non-invasive, and semi-invasive physical inspection methods. We study the shortcomings of countermeasures and develop more effective approaches.
e. Defense in depth
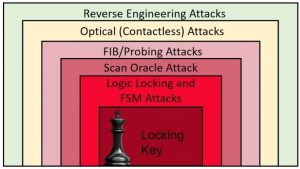
The security measures developed for hardware obfuscation schemes has always been a one-to-one exercise, where a security designer deploys specific technologies to counter an specific risk or attack. In system with only a single layer of dense, just a single error in design or implementation can lead to catastrophic compromise. Attackers are creative, threat are often not completely anticipated. Therefore, having a multiple countermeasure often become the difference between a secure or compromised system. Consequently developing a layered defense approach known as Defense-in-depth can be a more practical approach for addressing the security challenges in hardware security. The idea is also implemented in cybersecurity community to detect and prevent a malicious intruder in the system. We are working on the ideas to defend a system against any attack by deploying several independent protection methods thus raising the cost of attack. Therefore, the capability of obfuscated device to defend against malicious entity not only improve but also reduce the probability of intrusion through any other open door which was left open unintentionally.
Thermal Barrier Coatings (TBC)
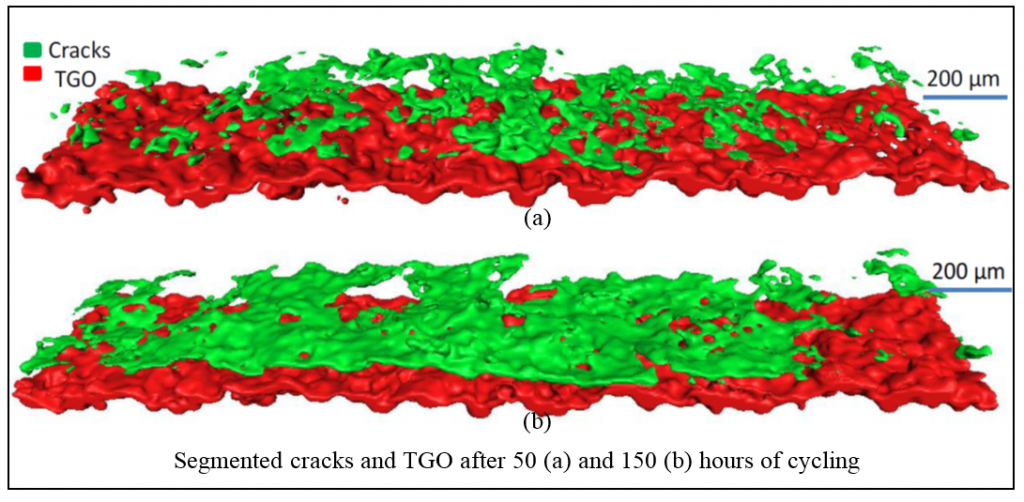
We have been investigating on 3D non-destructive imaging on TBCs to obtain desired information by X-ray tomography. In collaboration with Dr. Eric Jordan from University of Connecticut for the first time we could track the progress of the exact same crack after multiple rounds of thermal cycling in a TBC sample. We established a method for monitoring the progression and linkage behavior of cracking in the coating and use these information to answer very important questions about the most important mechanism which drives the failure of TBCs.
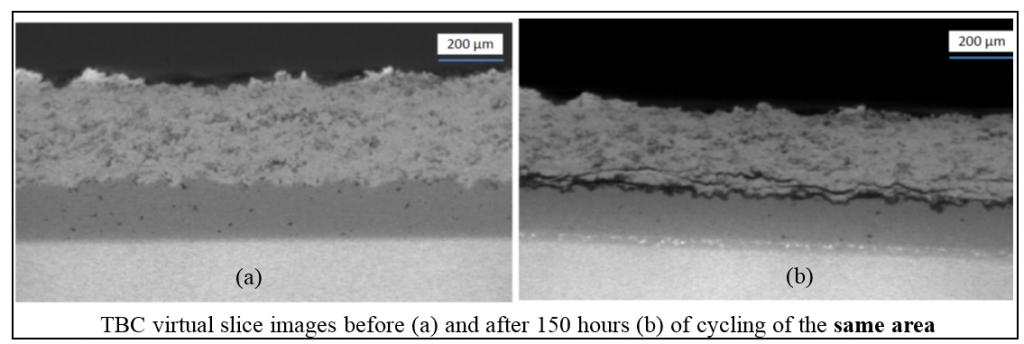
Using our advanced image processing capabilities, X-ray tomography files are segmented and crack growth behavior was very well captured. This can provide valuable information about the kinetics of spallation and interfacial surface geometry change. The availability of true interfacial surface change under the TBC will also allow more accurate FEM modelling of TBCs using simulations where previously oversimplifications such as assuming cracks as lines or assuming the interfacial geometry as sine waves have been made previously.
Sensors
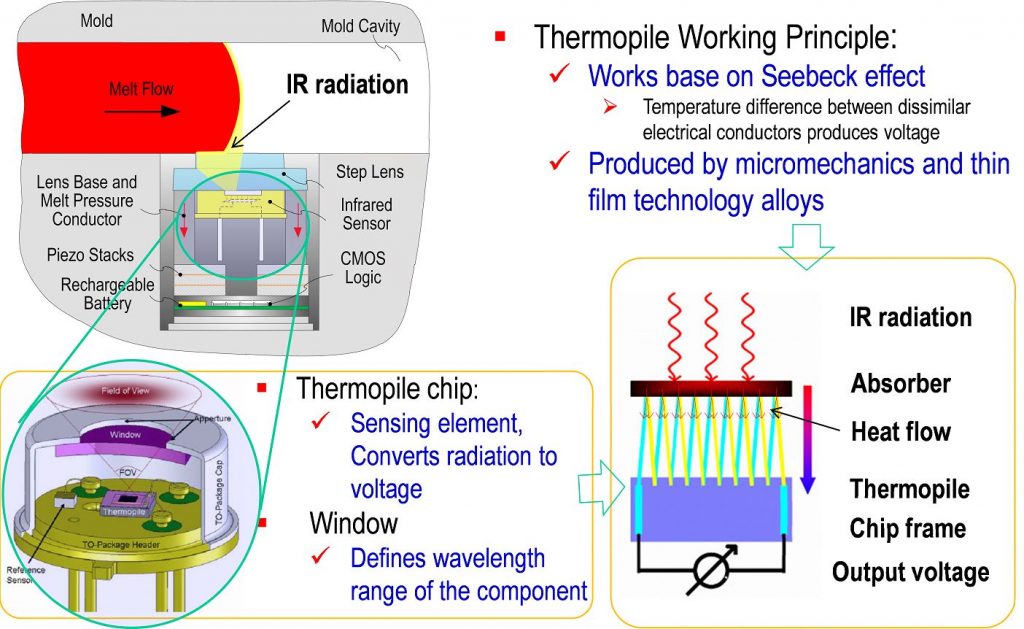
Online measurement of pressure, temperature, velocity, and viscosity of polymer melt within the injection mold is key to improving process control for quality assurance in injection molding. In this project a multivariate sensing method has been introduced to enable simultaneous determination of the four parameters in injection molding using one single sensor package.
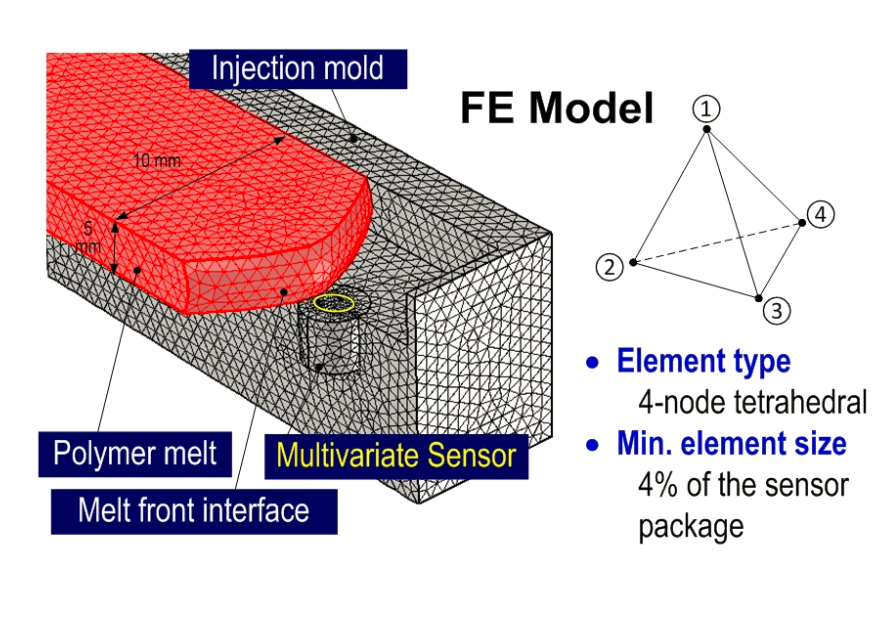
I simulated the polymer melt velocity sensing based on the melt temperature measured by an Infrared (IR) sensing element integrated within the sensor package. From the Stephan-Boltzmann model, an analytical relationship between the melt front velocity and the ramping rate of the IR detector voltage output has been established. Using a Finite Element (FE) model, the process of polymer melt flowing over the IR sensor lens has been simulated. The result shows that the melt front velocity can be determined within an error of ± 0.25%, under a broad range of melt temperature and IR detector diameters. The result is experimentally confirmed by temperature measurement in a realistic injection molding machine instrumented with a reference IR sensor.
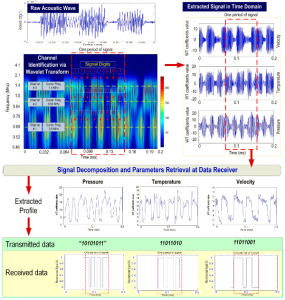
Wireless Communication
I have investigated the feasibility of employing acoustic waves as a tool for data communication between sensors inside a complex system and a receiver outside of the machine without wire connection. This is very beneficial for wireless communication between underwater systems or inside an injection molding machine, where cooling lines and many other features will make it really difficult to install a wired communication set up. The project was consisted of transmitter design, acoustic wave propagation simulation (using COMSOL) and conducting experimental tests on real injection molding machine in order to transmit three molding process parameters (pressure, temperature, and velocity), which are critical for estimating and controlling the quality of the final product.